Network and connectivity requirements for PostgreSQL environments
Overview
This topic covers the general network and connectivity requirements for the Delphix Engine, including connection requirements, port allocation, and firewall and Intrusion Detection System (IDS) considerations. For platform-specific network and connectivity requirements, see the relevant topics under the Requirements section for each platform.
General outbound from the Delphix engine port allocation
Protocol | Port Numbers | Use |
|---|---|---|
TCP | 25 | Connection to a local SMTP server for sending email |
TCP/UDP | 53 | Connections to local DNS servers |
UDP | 123 | Connection to an NTP server |
UDP | 162 | Sending SNMP TRAP messages to an SNMP Manager |
TCP | 443 | HTTPS connections from the Delphix Engine to the Delphix Support upload server |
TCP/UDP | 636 | Secure connections to an LDAP server |
TCP | 8415 | Connections to a Delphix replication target. See Configuring Replication |
TCP | 50001 | Connections to source and target environments for network performance tests. |
General inbound to the Delphix Engine port allocation
Protocol | Port Numbers | Use |
|---|---|---|
TCP | 22 | SSH connections to the Delphix Engine |
TCP | 80 | HTTP connections to the Delphix GUI |
UDP | 161 | Messages from an SNMP Manager to the Delphix Engine |
TCP | 443 | HTTPS connections to the Delphix Management Application |
TCP | 8415 | Delphix Session Protocol connections from all DSP-based network services including Replication, SnapSync for Oracle, V2P, and the Delphix Connector. |
TCP | 50001 | Connections from source and target environments for network performance tests via the Delphix CLI. See Network Performance Tool |
Firewalls and Intrusion Detection Systems (IDS)
Production databases on source environments (for dSources) are often separated from the non-production environment by firewalls. Firewalls can add milliseconds to the latency between servers. Accordingly, for best performance, there should be no firewalls between the Delphix Engine and the virtual database (VDB) target environments. If the Delphix Engine is separated from a source environment by a firewall, the firewall must be configured to permit network connections between the Delphix Engine and the source environments for the application protocols (ports) listed above.
Intrusion detection systems (IDSs) should also be made permissive to the Delphix Engine deployment. IDSs should be made aware of the anticipated high volumes of data transfer between dSources and the Delphix Engine.
SSHD Configuration
Target Unix environments are required to have sshd running and configured such that the Delphix Engine can connect over ssh.
The Delphix platform expects to maintain long-running, highly performant ssh connections with remote Unix environments.
Network and connectivity requirements for PostgreSQL
IP connections must exist between the Delphix Engine and the target environments.
The Delphix Engine uses an SSH connection to each target environment, NFS connections from each target environment to the Delphix Engine, and PostgreSQL client connections to the virtual databases on the target environment.
Once connected to a staging target environment through SSH, the Delphix Engine initiates a PostgreSQL replication client connection from the target environment to the source environment.
Port allocation for PostgreSQL environments
The following diagram describes the port allocations for PostgreSQL environments. It illustrates the ports that we recommend to be open from Delphix to remote services, to the Delphix Engine, and to the Target Environments.
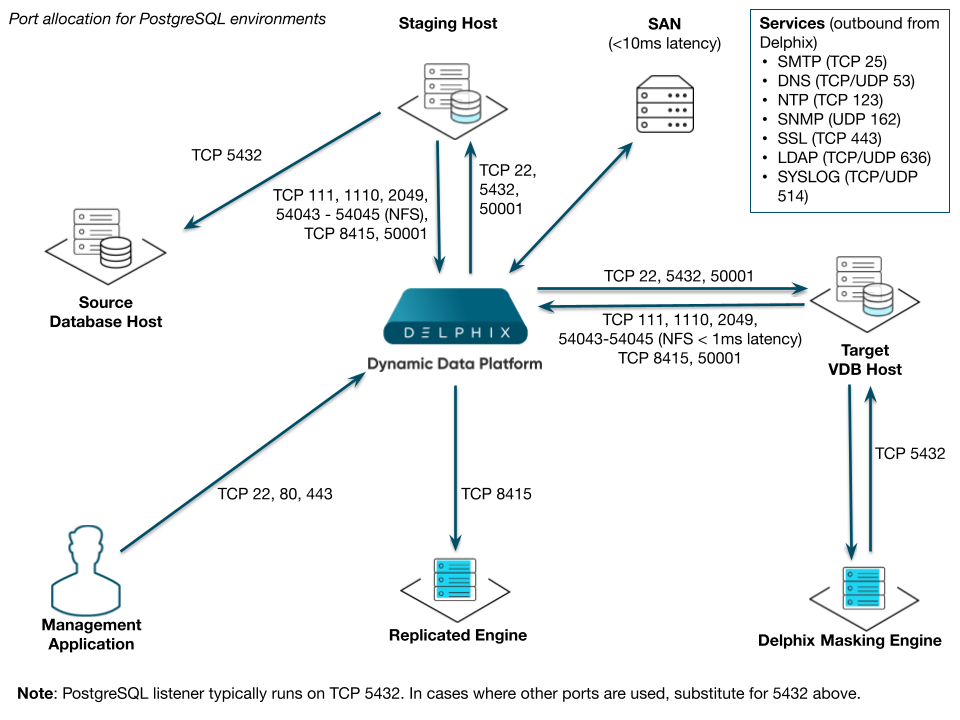
Outbound from the Delphix Engine port allocation
Protocol | Port Numbers | Use |
|---|---|---|
TCP | 22 | SSH connections to the target database environment |
TCP | xxx | PostgreSQL client connections to the PostgreSQL instances on the target environments (port 5432 by default) |
Inbound to the Delphix Engine port allocation
Protocol | Port Number | Use |
|---|---|---|
TCP/UDP | 111 | Remote Procedure Call (RPC) port mapper used for NFSv3 mounts |
TCP | 1110 | Network Status Monitor (NSM) client from target hosts to the Delphix Engine |
TCP | 2049 | NFS client from target hosts to the Delphix Engine (NFSv3 and NFSv4) |
TCP | 54043 | Client mount daemon (NFSv3 only) |
TCP | 54044 | Lock state notification service (NFSv3 only) |
TCP | 54045 | Network Lock Manager (NLM) client from target hosts to Delphix Engine (NFSv3 only) |
UDP | 33434 - 33464 | Traceroute from the target database server to the Delphix Engine (optional) |
Port allocation between source and staging target environments
Outgoing | Incoming | Protocol | Port Number | Use |
|---|---|---|---|---|
Target Environment | Source Environment | PostgreSQL replication client | xxx | PostgreSQL replication client connection to the PostgreSQL instances on the source environment (port 5432 by default) |
