Passing credentials securely to hook operations
Sometimes, commands in hook operations need credentials to perform tasks such as making API calls or managing local services. To avoid hard-coding credentials in the hook code, you can pass credentials securely to hooks via environment variables using a new list property of each hook operation. The elements in this list define a set of environment variables and the credentials to pass to the hook in those variables.
In the browser, the list can be viewed and updated in the Credential environment variables section of a hook operation. (Hook operations can be accessed in the dataset and hook template creation dialogs and view/edit pages.) For example, to view or edit hook credentials for a dataset:
Login to the Delphix management application.
Under Datasets, select a dSource or VDB.
Select the Configuration tab and then the Hooks tab.
Select a hook operation.
To make any changes, such as adding, modifying or deleting credentials, click on the edit icon to the right of Operation type.
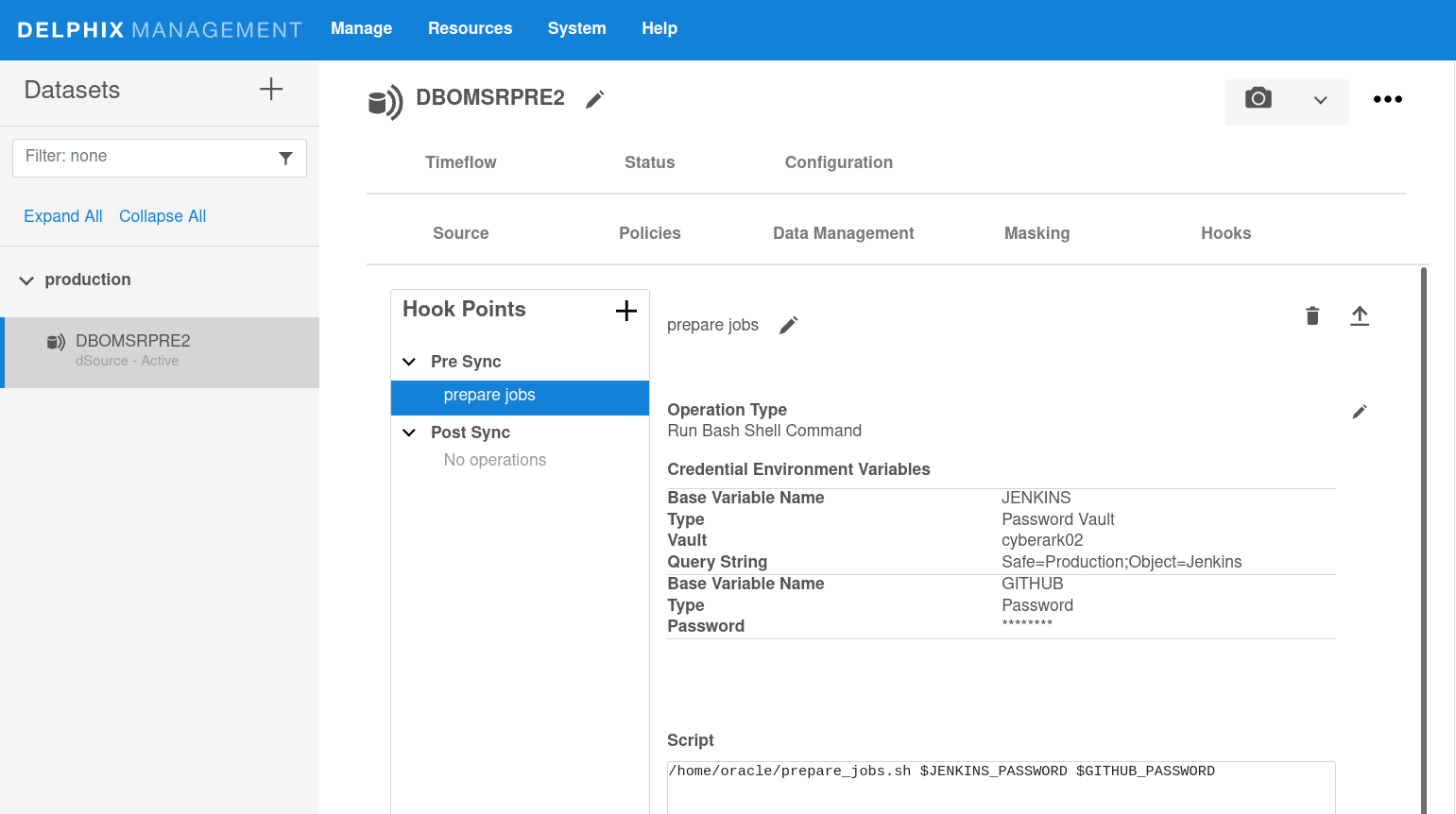
In the API and CLI, the credentials list property of each hook operation is an array called credentialsEnvVarsList.
Hook credentials can be configured directly as a password or key (entered by the user) or indirectly by selecting a password vault and a location in that vault. Credentials entered directly are managed securely by the engine in the same way as other passwords and keys, which are encrypted in disk and neither logged nor exposed by the API, whereas vault credentials are managed securely and externally to the engine by a specialized product such as CyberArk or HashiCorp Vault that has already been configured in the engine. Credentials stored in a vault are always retrieved by the engine just before executing the hook, so they will always contain the latest values. Any number of credentials of any type can be defined for an operation in the credentialsEnvVarsList property.
Four types of credentials can be defined for hooks:
CyberArkVaultCredentialHashiCorpVaultCredentialPasswordCredentialKeyPairCredential(supported only via the API and CLI at the moment)
For more information on each of these types, visit your engine's API page for that type at https://<engine address>/api/#<type name> (you must log in first).
To illustrate, consider a hook that needs to authenticate to two different APIs, one using an API key entered directly by the user and another using a username and password managed by a vault. The user can configure the credential variables as follows:
|
When this hook executes, it will receive two sets of environment variables containing the corresponding credentials: API1_PASSWORD with value API-KEY-02a0b73f and variables API2_USER and API2_PASSWORD containing the values stored in the vault MyCyberArk1 at the location of the provided query string. The API2 credentials are retrieved from the vault just before the hook executes, so they will always contain the latest values.
The complete list of environment variables that may be available to a hook is:
<base name>_USER: user name. Present only if the credentials are of a vault credential type and the entry in the vault contains a user name.<base name>_PASSWORD: a password. Present forPasswordCredential. Also present in case of a vault credential type and the vault entry contains a password.<base name>_PRIVKEY: a private key. Present forKeyPairCredential. Also present in case of a vault credential type and the vault entry contains a private key.<base name>_PUBKEY: a public key. Present forKeyPairCredential. Also present in case of a vault credential type and the vault entry contains a public key.
