Migrating a TDE-enabled vPDB
Migrating a TDE-enabled virtual pluggable database (vPDB) from one container database to another container database on the same target host or a different target host involves the following steps:
Disable the vPDB.
Migrate.
(Applicable only for software keystore based vPDB)
For a software keystore based vPDB, there are additional steps that are required before the enable. The steps are necessary because the keystore and exported keyfiles are not present on Delphix Continuous Data storage. These steps are:Copy the parent TDE keystore from the original target host to the new target host. If the vPDB is not being migrated to a new target host, then this step is not needed. Similarly, if the new host has the parent keystore in a different location, then the parent keystore path for the vPDB needs to be updated.
Copy the artifact directory for the vPDB from the original target host to the new target host. If the vPDB is not being migrated to a new host, then this step is not needed.
Ensure that the new target container has the TDE keystore password set.
Merge the original target keystore into the new target keystore. This is required to support a rewind operation to a snapshot taken before the migrate.
(Applicable only for OKV-enabled or HSM-enabled vPDB)
For a TDE OKV or HSM-enabled vPDB, additional steps are required before enabling. These steps are essential because the exported keyfiles are not present on Delphix Continuous Data Storage:Provide access to the vPDB master encryption key on the new target endpoint (refer to Oracle Key Vault documentation or CipherTrust Manager documentation).
Copy the artifact directory for the vPDB from the original target host to the new target host.
Ensure that the new target container has the TDE Key Manager Credential set.
Enable.
The diagram below illustrates the scenario of a migrated TDE-enabled vPDB.
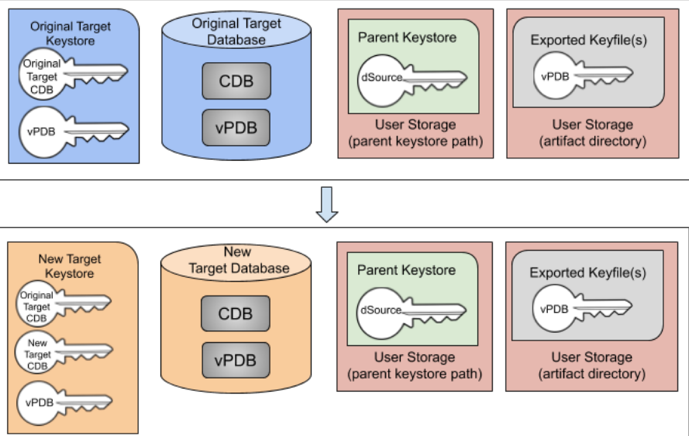
Migrated TDE-enabled vPDB (software-based key store)
Example for TDE software keystore based vPDB
Consider the following TDE software keystore based vPDB:
This vPDB is currently provisioned to the container database CDOMLOTG9620 on the host tde-target18. Connecting to that database, you can see the keys for the target container and the vPDB:
SQL> show pdbs
CON_ID CON_NAME OPEN MODE RESTRICTED
------ ---------------------- ---------- ----------
2 PDB$SEED READ ONLY NO
3 CDOMLOTG9620PDB1 READ WRITE NO
4 CDOMLOTG9620PDB2 READ WRITE NO
5 CDOMLOTG9620PDB3 READ WRITE NO
6 TDE_VPDB READ WRITE YES
SQL> select con_id, key_id from v$encryption_keys;
CON_ID KEY_ID
------ ----------------------------------------------------
1 ASFwmcfaMk8vv1LvzV0H8BEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
6 AdDdKibLKU9mv6PDAIvVvH0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAThe key for the target container starts with ASFwmcfa and the vPDB key starts with AdDdKibL. There is also an artifact directory for this vPDB found in <toolkit_directory>/oracle_tde_keystores:
$ ls /toolkit/oracle_tde_keystores/
tde_vpdb_Encrypted_e9d2befb-9849-43c8-85f5-5ee8b760e334Migrate this vPDB to the container database CDOMLOTGCAE8 located on the host tde-target18b. Currently, that container has the following configuration:
SQL> show pdbs
CON_ID CON_NAME OPEN MODE RESTRICTED
------ ---------------------- ---------- ----------
2 PDB$SEED READ ONLY NO
3 CDOMLOTGCAE8PDB1 READ WRITE NO
4 CDOMLOTGCAE8PDB2 READ WRITE NO
5 CDOMLOTGCAE8PDB3 READ WRITE NO
SQL> select con_id, key_id from v$encryption_keys order by con_id;
CON_ID KEY_ID
------ ----------------------------------------------------
1 Ad344VSUDk/jv1VDb1QNBHMAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
3 AetaL+IKpE+ov5avXouApwUAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
4 AXZTgaBbxk+6v6x2yHQ4ArgAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
5 AayTgbjkJE/3v82/hBBBAWEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAThe new target container has a CDB key starting with Ad344VSU. The migration steps are as follows:
Disable the vPDB in the original container on the host
tde-target18a.Migrate the vPDB to point to the new container on the new target host
tde-target18b. The UI will report the following warnings during the migrate operation, which indicate the manual steps which need to be done: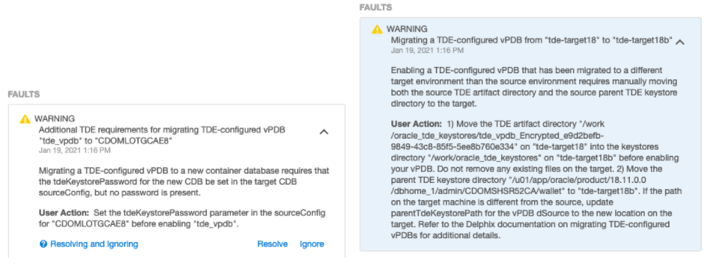
Set the TDE Keystore Password for the new target container
CDOMLOTGCAE8on the new target hosttde-target18b.Copy the parent keystore to the new target host
tde-target18b. In this case, keep the existing location/u01/app/oracle/product/18.11.0.0/dbhome_1/admin/CDOMSHSR52CA/walleton both hosts, so the configuration does not need to be updated.Copy the TDE artifact directory
/toolkit/oracle_tde_keystores/tde_vpdb_Encrypted_e9d2befb-9849-43c8-85f5-5ee8b760e334to the new target hosttde-target18b. If there are no TDE-enabled vPDBs on the new target host, theoracle_tde_keystoresdirectory may need to be created first.On the new target host, check if
/toolkit/oracle_tde_keystoresexists. Create it, if not. While creating the directory, you should make sure the group ownership is set tooinstalland the directory's permissions are set to0770. For example:CODEmkdir -p /toolkit/oracle_tde_keystores chgrp oinstall /toolkit/oracle_tde_keystores chmod 0770 /toolkit/oracle_tde_keystoresCopy the TDE artifact directory from the old target host to the new target host, preserving file permissions. For example, if using
scpon the new target host:CODEscp -rp <old_target_hostname>:/toolkit/oracle_tde_keystores/tde_vpdb_Encrypted_e9d2befb-9849-43c8-85f5-5ee8b760e334 /toolkit/oracle_tde_keystores/If the copied files are now owned by a user that is not the Oracle home owner, add group-write permissions to key export files to prevent key imports from failing with
ORA-46646: file from which keys are to be imported is invalid. For example:CODEfind /toolkit/oracle_tde_keystores/tde_vpdb_Encrypted_e9d2befb-9849-43c8-85f5-5ee8b760e334 -name "*.keys" -exec chmod g+w {} \;
Merge the original target keystore into the new target keystore. Oracle provides the
ADMINISTER KEY MANAGEMENT MERGE KEYSTOREcommand to facilitate this. Note that you cannot successfully merge into a keystore that is currently in use by the database, so the recommended process is to first copy the original target keystore to the new host, merge the two keystores into a new keystore, replace the existing new target keystore and finally bounce the CDB to start using the merged keystore:Copy the original keystore to
/tmp/tde-target18aontde-target18b.Create a temporary directory
/tmp/mergedontde-target18b.While connected to the new container on
tde-target18b, issue the merge keystore command:SQLSQL> administer key management merge keystore '/tmp/tde-target18a' identified by *** and keystore '/u01/app/oracle/product/18.11.0.0/dbhome_1/admin/CDOMLOTGCAE8/wallet' identified by *** into new keystore '/tmp/merged' identified by ***;Copy the new merged keystore
/tmp/merged/ewallet.p12into the existing keystore location ontde-target18b(backing up the existing keystore first).If there is an autologin wallet configured for the container, it must be recreated:
SQLSQL> administer key management create auto_login keystore from keystore '/tmp/merged' identified by ***;Copy the new merged autologin keystore
/tmp/merged/cwallet.ssointo the existing keystore location ontde-target18b(backing up the existing autologin keystore first).Shutdown and restart the new target container database on the host
tde-target18b.
Confirm that the keystore now contains both the original key and the new key:
CODESQL> select key_id from v$encryption_keys where con_id = 1; KEY_ID ---------------------------------------------------- ASFwmcfaMk8vv1LvzV0H8BEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA Ad344VSUDk/jv1VDb1QNBHMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHave the key starting with ASFwmcfa from the original container and the key starting with Ad344VSU from the new container.
Enable the vPDB to complete the migration operation. The vPDB is successfully started in the new container, with its key starting with AdDdKibL:
CODESQL> show pdbs CON_ID CON_NAME OPEN MODE RESTRICTED ------ ------------------------------ ---------- ---------- 2 PDB$SEED READ ONLY NO 3 CDOMLOTGCAE8PDB1 READ WRITE NO 4 CDOMLOTGCAE8PDB2 READ WRITE NO 5 CDOMLOTGCAE8PDB3 READ WRITE NO 6 TDE_VPDB READ WRITE NO SQL> select con_id, key_id from v$encryption_keys order by con_id; CON_ID KEY_ID ------ --------------------------------------------- 1 Ad344VSUDk/jv1VDb1QNBHMAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 1 ASFwmcfaMk8vv1LvzV0H8BEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 3 AetaL+IKpE+ov5avXouApwUAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 4 AXZTgaBbxk+6v6x2yHQ4ArgAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 5 AayTgbjkJE//v82/hBBBAWEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA 6 AdDdKibLKU9mv6PDAIvVvH0AAAAAAAAAAAAAAAAAAAAAAAAAAAAA 6 rows selected.
Example for TDE OKV-enabled vPDB
Consider the following TDE OKV-enabled vPDB:
This vPDB is currently provisioned to the container database CDOMSHTGCF36 on the host tde-okv-target19. Connecting to that database, you can see the keys for the target container and the vPDB:
SQL> show pdbs
CON_ID CON_NAME OPEN MODE RESTRICTED
---------- ------------------------------ ---------- ----------
2 PDB$SEED READ ONLY NO
3 VCDO_GOG READ WRITE NO
SQL> select con_id, key_id from v$encryption_keys;
CON_ID KEY_ID
---------- ------------------------------------------------------------
1 06CB1F66B0B76E4FFFBFA67F9B47C5DC0
3 069A375EE65D7D4FD9BF4604513679C807The key_id for the target container starts with 06CB1F66B0 and the vPDB key starts with 069A375EE6. There is also an artifact directory for this vPDB found in <toolkit_directory>/oracle_tde_keystores:
[oracle@ip~]$ ls /work/oracle_tde_keystores/
VCDO_GOG_Untitled_3f9c41d4-c123-42b4-ba36-56ef03ade746 Migrate this vPDB to the container database CDOMLOSR50BD located on the host tde-okv-source19. Currently, that container has the following configuration:
SQL> show pdbs
CON_ID CON_NAME OPEN MODE RESTRICTED
---------- ------------------------------ ---------- ----------
2 PDB$SEED READ ONLY NO
3 CDOMLOSR50BDPDB1 READ WRITE NO
4 CDOMLOSR50BDPDB2 READ WRITE NO
5 CDOMLOSR50BDPDB3 READ WRITE NO
SQL> select con_id, key_id from v$encryption_keys where con_id=1;
CON_ID KEY_ID
---------- ----------------------------------
1 06EC44AF4DD6FA4F49BF1D5C3267D3AEF4The new target container has a CDB key starting with 06EC44AF4. The migration steps are as follows:
Disable the vPDB in the original container on the host
tde-okv-target19.Migrate the vPDB to point to the new container on the new target host
tde-okv-source19. The UI will report the following warnings during the migration operation, which indicate the manual steps that need to be done: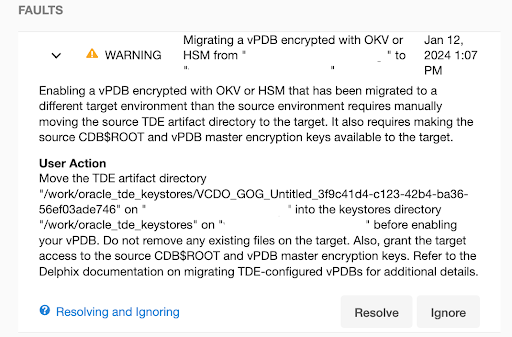
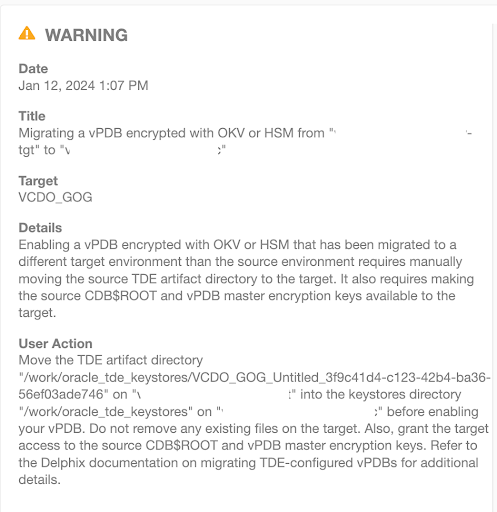
Set the TDE External Key Manager Credential for the new target container CDOMLOSR50BD on the new target host
tde-okv-source19if it is not already set. Please refer to Adding or Editing the TDE External Key Manager Credential.Grant the target access to the CDB$ROOT and vPDB master encryption keys (refer to Oracle Key Vault documentation) to add the members into the target virtual wallet.
Copy the TDE artifact directory
<toolkit_directory>/oracle_tde_keystores/VCDO_GOG_Untitled_3f9c41d4-c123-42b4-ba36-56ef03ade746to the new target hosttde-okv-source19. If there are no TDE OKV-enabled vPDBs on the new target host, theoracle_tde_keystoresdirectory may need to be created first.On the new target host, check if
<toolkit_directory>/oracle_tde_keystoresexists. Create it, if not. While creating the directory, you should make sure the group ownership is set tooinstalland the directory's permissions are set to0770. For example:CODEmkdir -p /work/oracle_tde_keystores chgrp oinstall /work/oracle_tde_keystores chmod 0770 /work/oracle_tde_keystoresCopy the TDE artifact directory from the old target host to the new target host, preserving file permissions. For example, if using
scpon the new target host:CODEscp -rp <old_target_hostname>:/work/oracle_tde_keystores/VCDO_GOG_Untitled_3f9c41d4-c123-42b4-ba36-56ef03ade746 /work/oracle_tde_keystores/If the copied files are now owned by a user that is not the Oracle home owner, add group-write permissions to key export files to prevent key imports from failing with
ORA-46646: file from which keys are to be imported is invalid. For example:CODEfind /work/oracle_tde_keystores/VCDO_GOG_Untitled_3f9c41d4-c123-42b4-ba36-56ef03ade746 -name "*.keys" -exec chmod g+w {} \;
Enable the vPDB to complete the migration operation. The vPDB is successfully started in the new container, with its key starting with 069A375EE6:
CODESQL> show pdbs CON_ID CON_NAME OPEN MODE RESTRICTED ---------- ------------------------------ ---------- ---------- 2 PDB$SEED READ ONLY NO 3 CDOMLOSR50BDPDB1 READ WRITE NO 4 CDOMLOSR50BDPDB2 READ WRITE NO 5 CDOMLOSR50BDPDB3 READ WRITE NO 6 VCDO_GOG READ WRITE NO SQL> select con_id, key_id from v$encryption_keys; CON_ID '06'||MKID ---------- ---------------------------------- 1 06EC44AF4DD6FA4F49BF1D5C3267D3AEF4 6 069A375EE65D7D4FD9BF4604513679C807
