Managing Cipher Suites for Connector
Introduction
Connector cipher management is a feature designed to control the ciphers used during the handshake process when establishing a connection with the host connector. The connector is installed independently from the Delphix Continuous Data Engine. However, to use this feature hosts must be added to the Delphix Continuous Data Engine first.
The feature supports updating the cipher configuration of all the Windows hosts added to the Delphix Continuous Data Engine in one go.
Additionally, the Get Host Connector Cipher API is available for use, which retrieves the current list of cipher suites used by a specific host.
Requirements and compatibility
Connector version: This feature requires connector version 1.37.0.0 or higher.
Target environment: The API can be applied to Windows target environments that have been added to the Delphix Continuous Data Engine.
Host status: The host must be enabled for the action to be successful.
Cluster support: Windows target cluster environments are supported for the Exclude API. To use the Get Connector Cipher operation, the relevant Windows target environment must be selected from the environment endpoint.
Design overview
The connector cipher management feature accepts a list of ciphers that need to be excluded and updates the PREFERREDCIPHERSUITES parameter in the connector property file accordingly. This update can be applied across all Windows hosts or only specified hosts if provided.
The API operates on all the Windows hosts when no specific host is mentioned. By connecting to each host through the connector connection itself, the API updates the preferred cipher list. This updated cipher suite will be then used for any subsequent connection establishment by the connector.
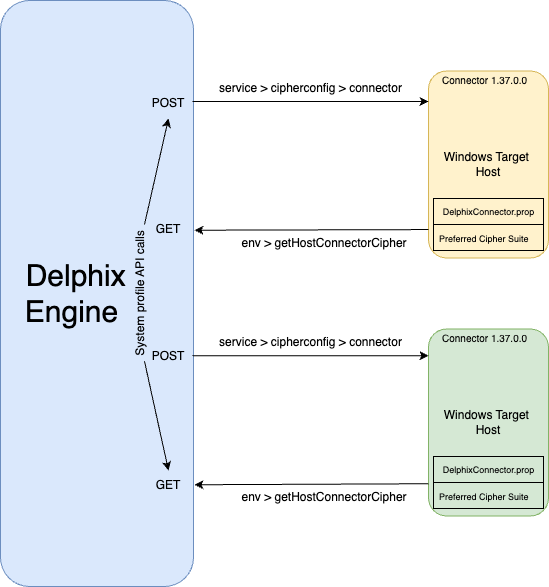
API functionality and application
The API can be accessed directly using the system user login and CLI.
API Object | Path | Type | Name | Description |
ConnectorCiphers
|
| API Type | ConnectorCiphers
|
|
SourceEnvironment |
| Operation | getHostConnectorCipher | Lists the ciphers configured in the host connector. |
ip-10-110-233-199> service cipherconfig connector
ip-10-110-233-199 service cipherconfig connector> ls
Operations
create
ip-10-110-233-199 service cipherconfig connector> create
ip-10-110-233-199 service cipherconfig connector create *> set excludeCiphers="TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384"
ip-10-110-233-199 service cipherconfig connector create *> set environments=win-tgt-cc-1.dlpxdc.co,win-tgt-cc-2.dlpxdc.co
ip-10-110-233-199 service cipherconfig connector create *> commit
Dispatched job JOB-23
CONNECTOR_CIPHERS_EXCLUDE job started.
CONNECTOR_CIPHERS_EXCLUDE job completed successfully.
ip-10-110-233-199 service cipherconfig connector> ip-10-110-233-199> environment
ip-10-110-233-199 environment> select win-tgt-cc-1.dlpxdc.co
ip-10-110-233-199 environment 'win-tgt-cc-1.dlpxdc.co'> getHostConnectorCipher
ip-10-110-233-199 environment 'win-tgt-cc-1.dlpxdc.co' getHostConnectorCipher *> commit
TLS_DHE_PSK_WITH_AES_256_GCM_SHA384, TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256,
TLS_ECDHE_PSK_WITH_CHACHA20_POLY1305_SHA256, TLS_DHE_PSK_WITH_AES_128_GCM_SHA256,
TLS_DHE_PSK_WITH_CHACHA20_POLY1305_SHA256, TLS_PSK_DHE_WITH_AES_128_CCM_8,
TLS_DHE_RSA_WITH_AES_256_CCM, TLS_DHE_PSK_WITH_AES_256_CCM,
TLS_ECDHE_ECDSA_WITH_AES_128_CCM_8, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_256_GCM_SHA384,
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_AES_128_GCM_SHA256, TLS_AES_256_GCM_SHA384,
TLS_CHACHA20_POLY1305_SHA256, TLS_AES_128_CCM_SHA256, TLS_AES_128_CCM_8_SHA256,
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384, TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA,
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA,
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,
TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256,
TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384, TLS_RSA_WITH_AES_256_GCM_SHA384,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,
TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
ip-10-110-233-199 environment 'win-tgt-cc-1.dlpxdc.co'> Adding new Windows target hosts to the Delphix Continuous Data Engine requires making a separate API call. The cipher suites configuration is reset to default when the connector is reinstalled or upgraded. In this case, the exclude ciphers API must be called again as needed.
