Configuring SNMP
This topic describes how to configure SNMP.
Starting with version 6.0.6.0 the Delphix Engine adds support for SNMP version 3 by implementing the User Security Model (USM) of the SNMP version 3 (SNMPv3) specification. Version 3 of SNMP adds stronger security compared to version 2.
When SNMP v2 is configured and enabled, SNMP v1 is also configured and enabled. Similarly, v2 is configured and enabled with v3. This is a known behavior of the net-snmp package used to implement SNMP on the engine.
USM replaces the community string as in SNMP version 2 with user records. The Delphix engine can both receive and send SNMP version 3 messages only by using the USM security model. The USM model provides more security over version 2 by hashing passwords and encrypting the payload.
The Delphix Engine includes an SNMPv3 agent that is only capable of responding to read-only operations, such as GET messages using the User Security Model. USM users can be configured via the GUI, CLI, or API. Each user is composed of a username, authentication password, authentication protocol, privacy password, and a privacy protocol.
The Delphix Engine is also capable of sending alerts and faults over SNMP with the User Security Model. Messages are sent identically as with SNMP version 2 except that the USM model is used to authenticate and encrypt the alert message against a customer's manager. Users will need to properly configure their managers to receive messages. The use of the test function can be used to test configuration.
Prerequisites
There are no prerequisites for enabling SNMP to provide system status. The following are prerequisites for sending alerts to an external SNMP manager.
At least one SNMP manager must be available and must be configured to accept SNMPv2 InformRequest notifications.
Delphix's MIB (Management Information Base) files must be installed on the SNMP manager or managers. These MIB files describe the information that the Delphix Engine will send out. They are attached to this topic.
File name | Content-type | File Size |
|---|---|---|
text/plain | 5 kB | |
text/plain | 0.8 kB |
Configuring SNMP for v2
On the Delphix Engine login screen, select Delphix Setup.
In the Delphix Setup login screen, enter the sysadmin username and password.
Click Log In.
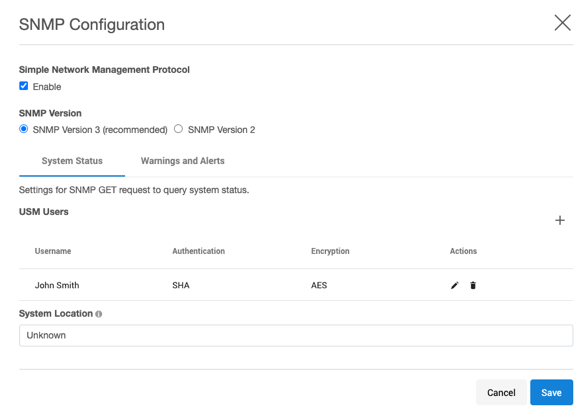
From the Delphix Setup, select Preferences > SNMP Configuration.
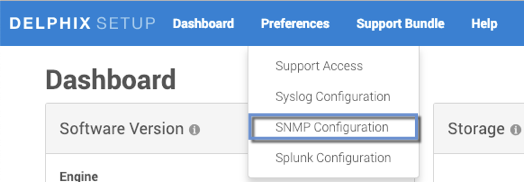
Select Enable.
Select SNMP Version 2.
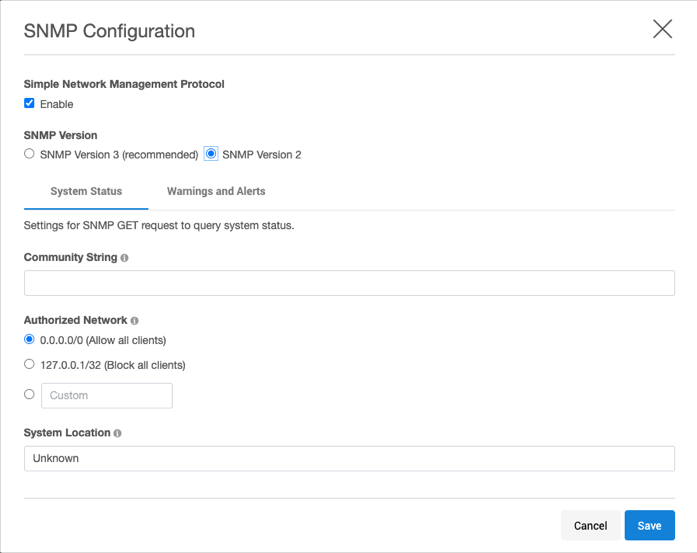
In Community string, enter the community string. It is the string that SNMP clients must provide in order to be authorized to retrieve SNMP information from the Delphix Engine.
OPTIONAL: change the following settings:
Authorized network – The set of client IP addresses (in CIDR notation) authorized to retrieve SNMP information from the Delphix Engine. To allow all clients, set this to 0.0.0.0/0 (the default). To prevent all clients from connecting, set this to the loopback address, 127.0.0.1/32.
System location – A free-form text description of the Delphix Engine's physical location. This is provided as the value for MIB-II OID.
Click Save to commit the SNMP configuration.
Configuring SNMP for v3
On the Delphix Engine login screen, select Delphix Setup.
In the Delphix Setup login screen, enter the sysadmin username and password.
Click Log In.
From the Delphix Setup, select Preferences > SNMP Configuration.
Select Enable.
Select SNMP Version 3 (recommended).
Click Save to commit the SNMP configuration.
Configure SNMP version 3 agent
After enabling SNMP and choosing version 3, the SNMP agent can be configured with the User Security Model (USM) users.
Click on System Status.
Click on the + to show the New SNMP USM User Information dialog.
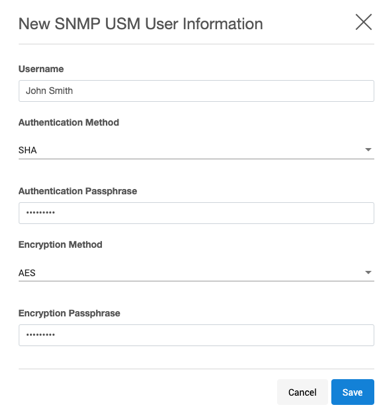
Provide the following information for the user:
Username - A string representing the name of the user.
Authentication method - An indication of whether messages sent on behalf of this user can be authenticated, and if so, the type of authentication protocol that is used. Users can select from:
MD5 -the HMAC-MD5-96 authentication protocol.
SHA -the HMAC-SHA-96 authentication protocol.
Authentication p
assphrase - If messages sent on behalf of this user can be authenticated, this key will be used with the authentication key for use with the authentication. This field requires a minimum of 8 characters.
Encryption method - Provides support for data confidentiality. The designated portion of an SNMP message is encrypted and included as part of the message sent to the recipient. Users can select from
AES - Advanced Encryption Standard
DES - Data Encryption StandardEncryption passphrase - If messages sent on behalf of this user can be encrypted, this key will be used with the encryption method for use with the authentication. This field requires a minimum of 8 characters.
Click Save to add your user.
Configuring SNMP version 3 managers
Click on the Warnings and Alerts tab.
Choose the Severity of the alerts that are sent via SNMP. The severity is ranked in order from most restrictive to least restrictive: critical, warning, and informational. Setting the severity critical will only include critical alerts while setting to informational will cause an informational, warning and critical alerts to be sent over SNMP to all managers.
Click + to add a manager to show the New SNMP manager information dialog.
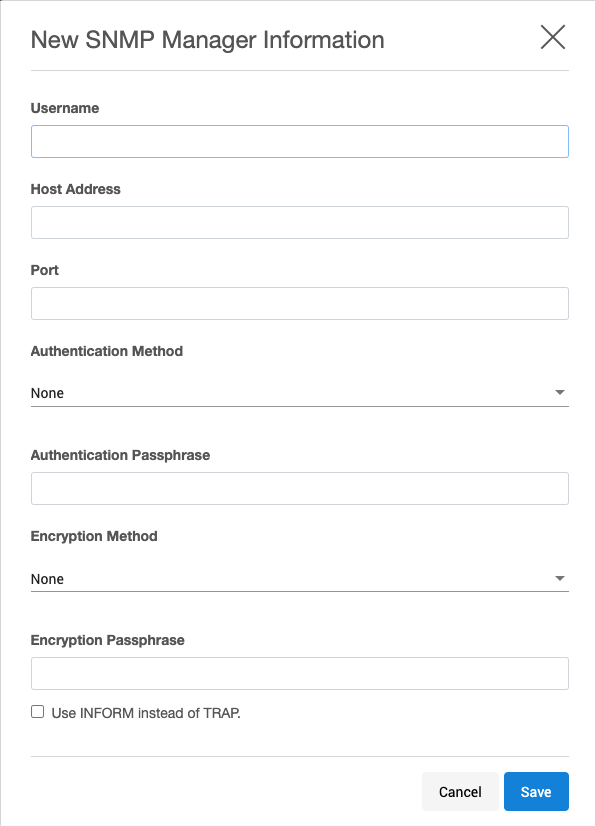
Provide the following information:
Username - A string representing the name of the user.
Host address - Host or IP address.
Port - Port used by the SNMP Engine.
Authentication method - An indication of whether messages sent on behalf of this user can be authenticated, and if so, the type of authentication protocol that is used. Users can select from:
MD5 -the HMAC-MD5-96 authentication protocol.
SHA -the HMAC-SHA-96 authentication protocol.
Authentication passphrase - If messages sent on behalf of this user can be authenticated, this key will be used with the authentication key for use with the authentication. This field requires a minimum of 8 characters.
Encryption method - Provides support for data confidentiality. The designated portion of an SNMP message is encrypted and included as part of the message sent to the recipient. Users can select from
AES - Advanced Encryption Standard
DES - Data Encryption StandardEncryption passphrase - If messages sent on behalf of this user can be encrypted, this key will be used with the encryption method for use with the authentication. This field requires a minimum of 8 characters.
By default, TRAP messages are sent and require the agent's authoritative engine id for the user to be configured with the SNMP engine ID from the Delphix Engine, which can be obtained via the CLI. Click Use Inform instead of Trap to use INFORM messages, which are more reliable and require less configuration at the expense of higher network traffic.
Click Save.
CLI: viewing SNMP engine ID
Viewing SNMP Engine ID
> service snmp v3
service snmp v3> ls
Properties
type: SNMPV3Config
enabled: true
engineId: 0x80001f88801ad80b5e62a7f85f00000000
location: Unknown
securityModel: USM
severity: WARNING
Children
manager
usm
Operations
updateSupported MIBs
The Delphix software can be configured to send SNMP traps when Delphix alerts are generated as described in the procedure above. In order to process these traps in your SNMP manager software, you will need the base Delphix MIB and the Delphix Alert MIB.
In addition to generating traps, the Delphix Engine supports read-only access to the following MIBs for basic system monitoring purposes.
The following MIB-II object hierarchies are defined in RFC 1213:
system (OID .1.3.6.1.2.1.1): Provides basic system identity information
interfaces (OID .1.3.6.1.2.1.2): Provides network interface information including I/O statistics
IP (OID .1.3.6.1.2.1.4): IP protocol information including IP addresses configured, routes, and IP statistics
The following UCD objects defined in http://www.net-snmp.org/docs/mibs/ucdavis.html
memory usage (OID .1.3.6.1.4.1.2021.4)
CPU usage (OID .1.3.6.1.4.1.2021.11)
Disk I/O statistics (OID .1.3.6.1.4.1.2021.13.15)
Examples
The following examples assume that you have enabled SNMP on a Delphix Engine named example.company.com, and have set the community string to "public".
Walking the MIB-II objects using the net-snmp snmpwalk tool:
CODE$ snmpwalk -v 2c -c public example.company.com SNMPv2-MIB::sysDescr.0 = STRING: Delphix Engine 5.1.6.0 DelphixOS 5.1.2017.03.24 SNMPv2-MIB::sysObjectID.0 = OID: SNMPv2-SMI::enterprises.41028 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (476432) 1:19:24.32 SNMPv2-MIB::sysContact.0 = STRING: administrator@company.com SNMPv2-MIB::sysName.0 = STRING: example.company.com SNMPv2-MIB::sysLocation.0 = STRING: VM Host ...Walking Disk read and write I/O statistics:
CODE$ snmpwalk -v 2c -c public example.company.com .1.3.6.1.4.1.2021.13.15.1.1.12 UCD-DISKIO-MIB::diskIONReadX.1 = Counter64: 11310593921 UCD-DISKIO-MIB::diskIONReadX.2 = Counter64: 334 UCD-DISKIO-MIB::diskIONReadX.3 = Counter64: 334 UCD-DISKIO-MIB::diskIONReadX.4 = Counter64: 865912605 UCD-DISKIO-MIB::diskIONReadX.5 = Counter64: 867599133 UCD-DISKIO-MIB::diskIONReadX.6 = Counter64: 865339677 UCD-DISKIO-MIB::diskIONReadX.7 = Counter64: 11309258752 UCD-DISKIO-MIB::diskIONReadX.8 = Counter64: 0 UCD-DISKIO-MIB::diskIONReadX.9 = Counter64: 1822880256 seb-laptop:~$ snmpwalk -v 2c -c public example.company.com .1.3.6.1.4.1.2021.13.15.1.1.13 UCD-DISKIO-MIB::diskIONWrittenX.1 = Counter64: 22337830400 UCD-DISKIO-MIB::diskIONWrittenX.2 = Counter64: 0 UCD-DISKIO-MIB::diskIONWrittenX.3 = Counter64: 0 UCD-DISKIO-MIB::diskIONWrittenX.4 = Counter64: 45118203392 UCD-DISKIO-MIB::diskIONWrittenX.5 = Counter64: 45137660928 UCD-DISKIO-MIB::diskIONWrittenX.6 = Counter64: 45139064320 UCD-DISKIO-MIB::diskIONWrittenX.7 = Counter64: 22337830400 UCD-DISKIO-MIB::diskIONWrittenX.8 = Counter64: 0 UCD-DISKIO-MIB::diskIONWrittenX.9 = Counter64: 33023515648Retrieving the system uptime:
CODE$ snmpget -v 2c -c public example.company.com .1.3.6.1.2.1.1.3.0 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (1453172) 4:02:11.72
