Upgrade prerequisites
Version compatibility and support pre-checks
Please refer to Upgrade matrix before upgrading to a newer version.
Customers running version 5.3.9 and earlier that are requesting an upgrade to 6.0.0.0 and above, please contact Delphix Support to help coordinate this upgrade.
Upgrading from 6.0.x to 6.0.x includes pre-checks packaged in the upgrade image, contacting Delphix Support for this upgrade is not required (e.g. 6.0.0.0 → 6.0.9.0).
Scheduling downtime
To determine if an upgrade will require a reboot and VDB downtime refer to Upgrade matrix.
If the OS will not be updated as part of the upgrade, then the upgrade process will have no impact on the availability of VDBs, and you do not need to schedule any downtime for your VDB applications.
If the OS will be updated as part of the upgrade, then you should schedule appropriate downtime for your VDB applications. The Delphix Engine will automatically disable VDBs and dSources during the upgrade. The length of the downtime will be proportional to the number of VDBs.
Long-running jobs including replication and SnapSync will fail during any upgrade.
The upgrade file for the version to which you want to upgrade should be downloaded from the Delphix download site. From 6.0.2.0 onwards, the upgrade images are packaged with the latest version of upgrade pre-checks. Please use the latest upgrade image from the download site since the checks will be updated on a need-by basis.
Delphix Upgrade images are approximately 5GB in size; it is recommended to have both a fast internet connection to the Delphix download site as well as to the Delphix Engine.
The upgrade image should be downloaded or moved to a location accessible to the computer used for navigating the Delphix Management application.
Upgrading replication source
Delphix Engines can only perform replication to engines on the same or higher version. Upgrading a replication source without upgrading its replication targets could cause replication between those peers to fail.
Verifying the integrity of the downloaded upgrade image
SHA256 checksums can be used to verify the integrity of files downloaded via download.delphix.com. The sha256sum checksum listed next to each download will help ensure that a file has not changed as a result of a faulty file transfer, a disk error, or non-malicious meddling.
To calculate the checksum of downloaded files and compare them to the checksum listed on the download portal, the following utilities can be used:
On Windows,
certutil -HashFile <upgrade.tar.gz> SHA256On macOS or Unix servers with Perl installed,
shasum -a 256 <upgrade.tar.gz>On Unix servers with
coreutilsinstalled,sha256sum <upgrade.tar.gz>.
Verifying connectivity to datasets and environments
For Upgrades from versions > 5.3.6.0 and <6.0.0.0, your Delphix Engine will automatically quiesce all VDBs and dSources during the upgrade process in order to safely reboot to the new version.
For Upgrades from versions >= 6.0.0.0, based on the Upgrade matrix you can choose to postpone the VDB downtime and update just the running stack and related packages by choosing "Delay the Restart" option. You can update the OS at a later date by completing the upgrade.
At the end of the upgrade process, the Delphix Engine will also update the Delphix platform toolkit on each connected environment.
To perform these tasks, the Delphix Engine must be able to connect to the environments in which datasets exist and must have credentials to connect to datasets or applications. Environments involved must be properly configured to enable script execution.
When an environment, dataset, or application is unreachable or misconfigured, the upgrade may encounter access errors, and may not be able to re-start it after the upgrade has been applied.
If you know that a dataset is unavailable for some reason (e.g. host not reachable on the network, or the hosting server is down), it is recommended that you disable it (if necessary utilize Force Disable).
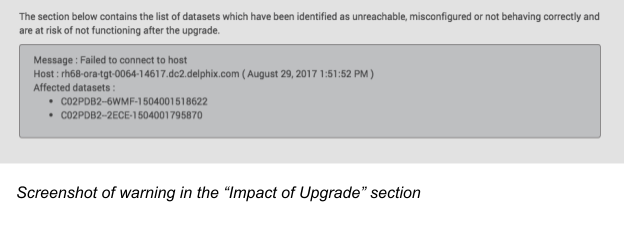
The Impact of Upgrade section in the Details tab contains the list of datasets that have been identified as unreachable, misconfigured or not behaving correctly and are at risk of not functioning after the upgrade.
Review the warnings in this section (if any) and take appropriate actions before applying the upgrade.