Data communication encryption
The Delphix Continuous Data Engine facilitates data communication with VDB target environments and staging environments via NFS for Linux environments and iSCSI for Windows environments. The system provides the flexibility to encrypt these communications as needed.
Feature limitations
NFS Encryption limitations (For Linux environments):
NFS encryption is not compatible with Oracle dNFS.
NFS encryption is not compatible with NFSv3.
iSCSI Encryption limitations (For Windows environments):
Windows clusters are not yet supported.
Windows standalone sources are not supported, as they use a connector environment (target environment) for iSCSI transactions and storage. Therefore, encryption of the source can be achieved by enabling encryption in the connector environment.
Prerequisites
The following operating systems are supported:
CentOS 7 and later
RHEL 7 and later
SUSE 12 and 15
All Delphix-supported Windows OSes. Forr more information, refer MySQL support matrix.
The designated network port for the specified feature in the Delphix Continuous Data Engine is 54046 for NFS and 53261 for iSCSI. The connection to these ports is initiated from the host to the Delphix Continuous Data Engine, constituting an ingress connection from the perspective of the Delphix Continuous Data Engine. For more information on network connectivity requirements, refer to Network connectivity requirements.
Feature design
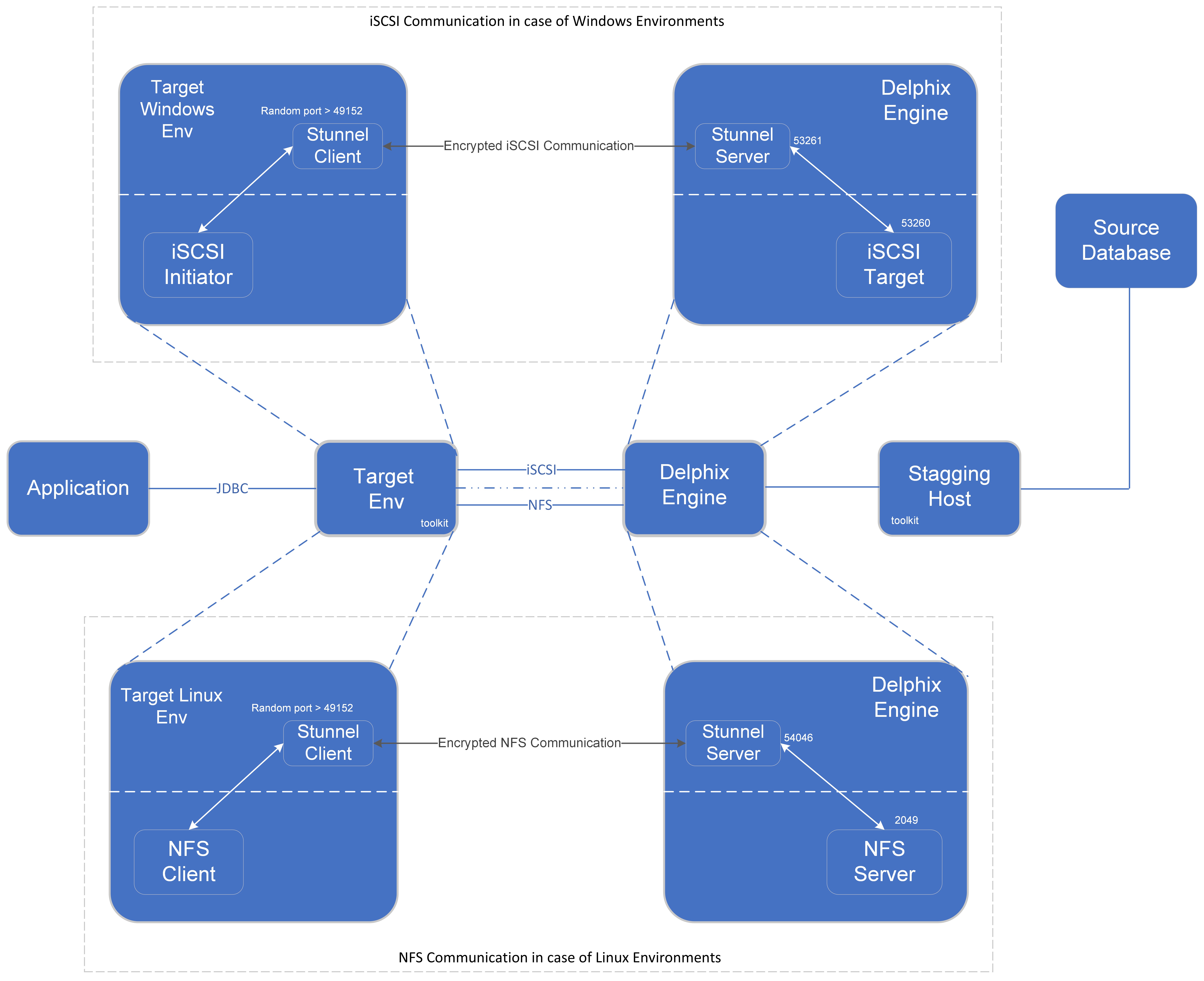
Image 1. NFS - Architecture
Encryption can be applied to secure data transfer between the Delphix Continuous Data Engine and the target VDB or staging source environment via NFS/iSCSI. This feature allows you the flexibility to enable or disable data communication (i.e. NFS/iSCSI communication) encryption on a per-environment basis.
Stunnel is used for this purpose. Stunnel is a utility that provides TLS tunneling capabilities in user space. The implementation involves configuring two Stunnel services to establish a secure TLS connection: one acting as a server and the other as a client. The client is configured to listen on a local port, enabling secure tunneling of any connections made to that port to the remote peer Stunnel application running on the server.
Implementation
The Encryption parameter can be activated for the specific environment either through the environment page or using the command-line interface (CLI). For more information about using the CLI, refer to the CLI guide.
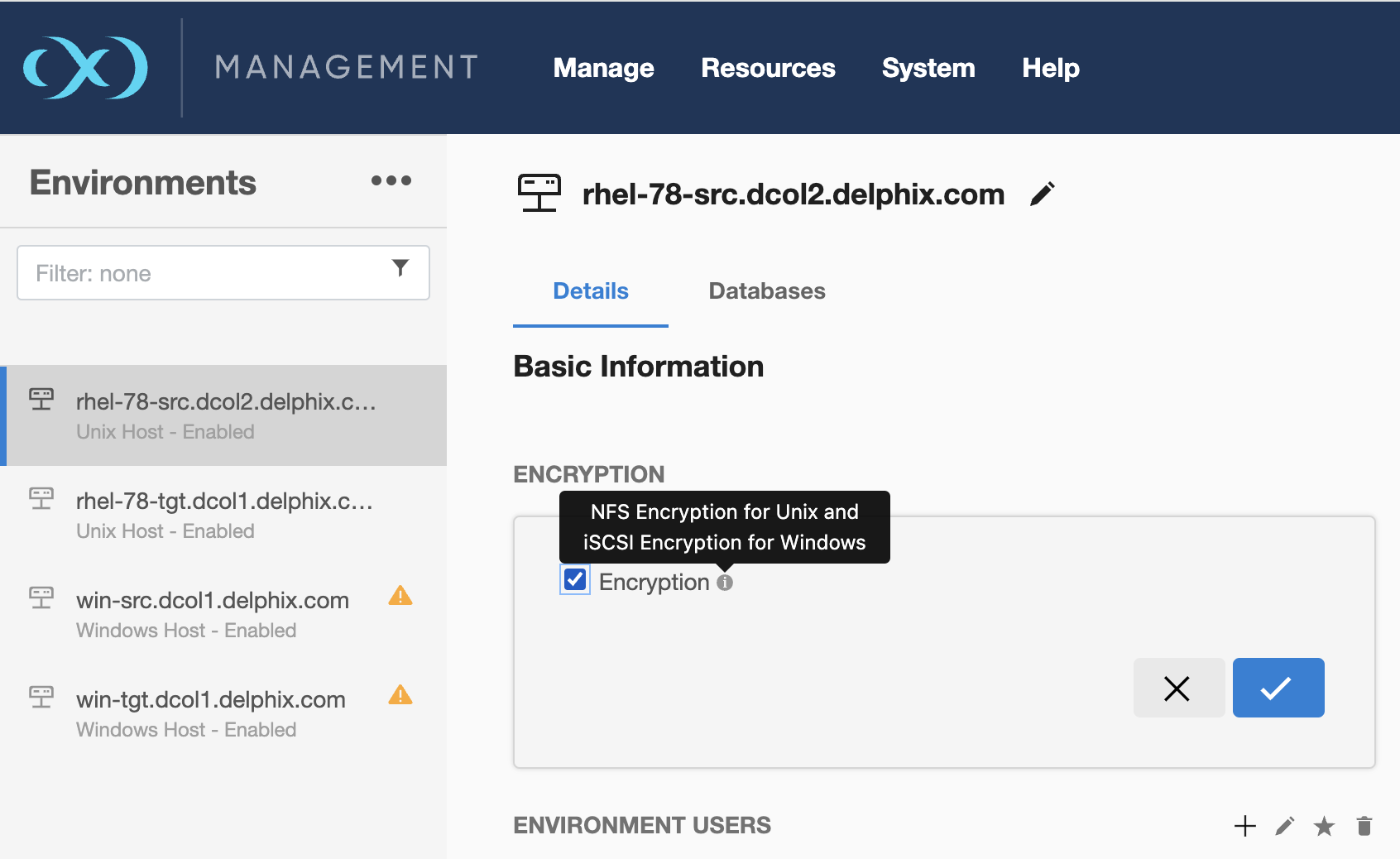
Image 2. Linux Environment Page
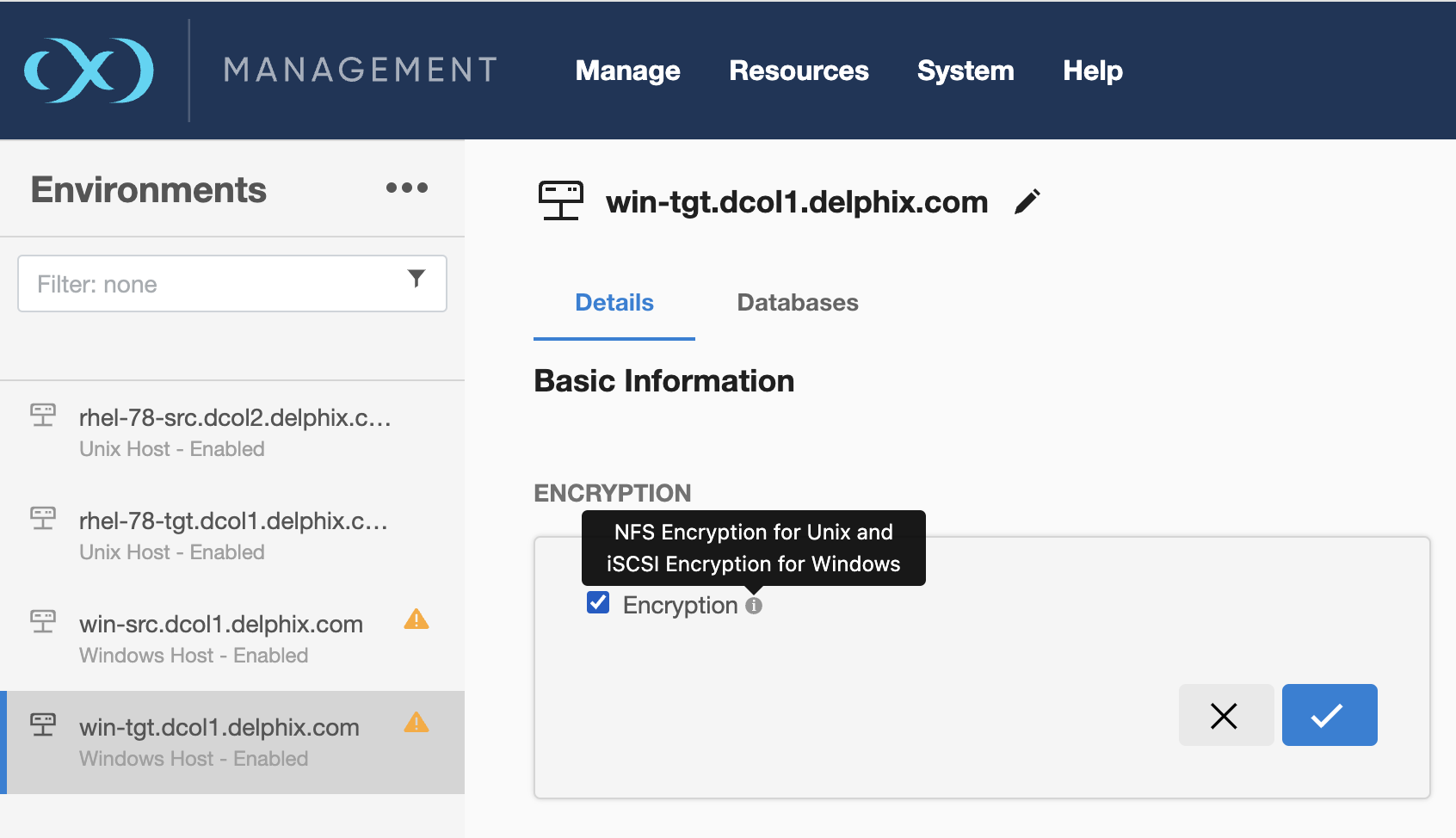
Image 3. Windows Environment Page
Before activating encryption, it's essential to confirm that all datasets linked to the environment are disabled.
Once environment encryption is enabled, you must enable all the relevant datasets. To verify whether a dataset is encrypted, you can check its environment's encryption status. All sources within an environment can either be encrypted or unencrypted, without any other state. For Linux environments, the encryption status of datasets can also be viewed in the status tab. To disable or enable all the associated datasets, APIs are available at the environment level. For specific API details and changes, refer to API Changes in Delphix 17.0.0.0.
Stunnel for encryption (deployment and configuration)
Stunnel is employed for Data Encryption, as illustrated in the image for feature design above. The Stunnel executable and required resources are deployed to the host via the toolkit. A new working directory is created on the host and Stunnel functions from that location. A randomly generated port is employed to configure Stunnel on the host. Upon disabling this feature, the Stunnel process is terminated, and the working directory is removed from the host.
In cases where a host is connected to more than one Delphix Continuous Data Engine with encryption enabled, it is possible to observe multiple Stunnel working directories and stunnel process on the host.
In the case of the Oracle cluster, the stunnel toolkit is set up, and the stunnel process is initiated on all active nodes when enabling this feature. Upon disabling the feature, the stunnel process is terminated, and the stunnel toolkit is uninstalled from all active nodes in the cluster.
Furthermore, when creating or enabling a node with this feature turned on for the cluster, the stunnel toolkit is configured, and the stunnel process is initiated on that specific node. If the feature is later turned off or the node is removed, the stunnel process is stopped, and the stunnel toolkit is removed from that individual node.
As Windows cluster is not supported, the encryption enabling feature is not available for cluster environments. Attempting to enable encryption on any cluster node environment that is part of a cluster will result in an error. Additionally, if encryption is enabled on an environment, adding that environment to a cluster as a node will fail.
Certificate usage for Stunnel communication
On the setup page, a new certificate for the stunnel-server has been seamlessly integrated and this integration is fully automated, eliminating the need for any user intervention. The process for replacing this certificate is similar to the process of replacing another certificate on the setup page. For more details, refer to Customer provided key pair configuration.
Upon enabling encryption for an environment, the stunnel working directory is established. Essential files are then transferred from the common toolkit directory to this newly created directory. Additionally, a required certificate is generated with a 730-day expiration period in real-time and is subsequently transferred to the host. This process facilitates the establishment of stunnel communication.
Changing a CA certificate chain along with a stunnel certificate update can result in downtime if the subject and issuer credentials are the same as the old CA certificate. The duration of the downtime is proportional to the number of encrypted environments. During this downtime, functions that involve mounting such as snapshot creation, VDB enable/disable, and VDB refresh, will not work due to the stunnel certificate replacement.
When you refresh the environment with encryption enabled, a new certificate is generated and uploaded to the host. This process effectively extends the expiry, ensuring continued secure communication.
Configuring ciphersuites
The default ciphersuite used for stunnel communication is TLS_CHACHA20_POLY1305_SHA256. If needed, you can change it to one of the following options: "TLS_AES_256_GCM_SHA384", "TLS_AES_128_GCM_SHA256", "TLS_AES_128_CCM_8_SHA256", or "TLS_AES_128_CCM_SHA256" using the provided API.
Details | Path | Visibility | Availability |
|---|---|---|---|
Env Encryption Ciphersuite |
| System | CLI |
Env Encryption Ciphersuite |
| System | CLI |
The endpoint /service/nfs/encryption is unavailable from version 22.0.0.0 onwards.
When altering the ciphersuite used for Encryption, any changes to the ciphersuite automatically trigger adjustments in the transport layer. This process eliminates the need for additional modifications or manual service restarts.
Diagnostic data
The environment monitoring system is implemented to assess the operational status of active stunnel connections and trigger the necessary alerts and fault notifications in case of any identified issues. However, assuming all configurations are in order, it can also restart the stunnel process if it unexpectedly stops.
Additionally, for diagnostic purposes, it should be noted that:
NFS encrypted mounts will be associated with the loopback IP address (127.0.0.1), while non-encrypted mounts will use the Delphix Continuous Data Engine's IP.
iSCSI encrypted connections will be connected with the loopback IP address (127.0.0.1), while non-encrypted iSCSI connections will use the Delphix Continuous Data Engine's IP.
API Usage
The following APIs are integrated for broad applicability, proving particularly advantageous when setting up NFS/iSCSI encryption in an environment.
Details | Path | Visibility | Availability |
|---|---|---|---|
Enable all datasets for an environment |
| Admin | CLI |
Disable all datasets for an environment |
| Admin | CLI |
