Other operations
This page introduces the RunExpect operation, designed for automating interactions with interactive programs like SSH in a Unix environment. It describes the use of environment variables for script execution, particularly those associated with dSources or VDBs. Guidance on passing credentials securely to hook operations and managing these credentials through the Delphix UI, API, and CLI, including steps for adding, modifying, or deleting credentials in hook operations is also included.
RunExpect operation
Executes an
expectscript in a Unix environment, utilizing the Expect utility for automating interactions with typically interactive programs likessh.Runs as the environment user from their home directory.
The Delphix Continuous Data Engine logs all output, displaying it in both the Delphix Management application and CLI for debugging purposes.
Success criteria: The script must exit with an exit code of 0. Other exit codes indicate failure.
RunExpect operation example
spawn ssh user@delphix.com
expect {
-re {Password: } {
send "${env(PASSWORD_ENVIRONMENT_VARIABLE)}\n"
}
timeout {
puts "Timed out waiting for password prompt."
exit 1
}
}
exit 0Environment variables
Operations executing user-provided scripts have access to OS environment variables.
For operations associated with dSources or VDBs, specific environment variables are set:
DLPX_DATA_DIRECTORY: The user-provided mount path on the UI.USER: The OS user used for linking the dSource/VDB.
Environment variables available to hooks
<base name>_USER: Username, present for vault credentials with a username.<base name>_PASSWORD: For PasswordCredential and vault credentials with a password.<base name>_PRIVKEY: Private key for KeyPairCredential and vault credentials with a private key.<base name>_PUBKEY: Public key for KeyPairCredential and vault credentials with a public key.
Secure credential management
Pass credentials securely to hook operations to perform tasks like API calls or service management.
Credentials are passed via environment variables in a hook operation's list property.
View or update credentials in the Credential Environment Variables section in the Delphix Continuous Data Engine UI.
Credential management steps
Log in to the Delphix Continuous Data Engine UI.
Under Datasets, select a dSource or VDB.
Go to Configuration → Hooks, then select a hook operation.
To add, modify, or delete credentials, click the edit icon next to Operation type.
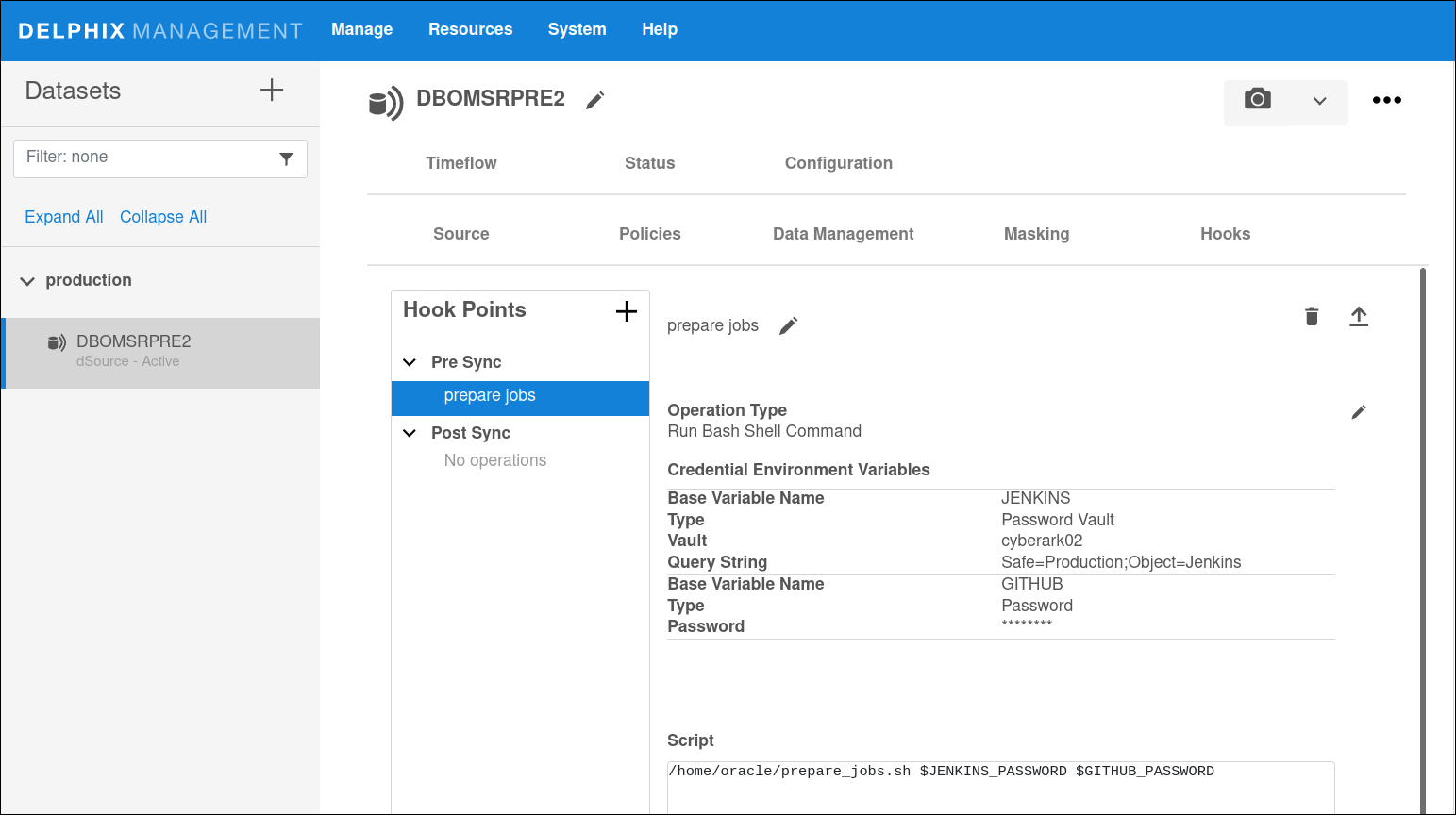
Credentials in the Credential Environment Variables section are declared using a Base Variable Name followed by
_PASSWORD.For example, variables JENKINS and GITHUB are used as
$JENKINS_PASSWORDand$GITHUB_PASSWORD.
API and CLI credential configuration
The credentials list property in the API and CLI is
credentialsEnvVarsList.Credentials can be direct (password or key) or indirect (password vault).
Direct credentials are managed securely and encrypted; vault credentials are retrieved just before execution.
Four credential types:
CyberArkVaultCredential,HashiCorpVaultCredential,PasswordCredential,KeyPairCredential(API and CLI only).
Example configuration through CLI
delphix source "pomme" update operations postRefresh *> edit 0.credentialsEnvVarsList
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList *> add
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 0 *> set baseVarName=API1
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 0 *> edit credentials
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 0 credentials *> set type=PasswordCredential
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 0 credentials *> set password="API-KEY-02a0b73f"
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 0 credentials *> back
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList *> add
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 *> set baseVarName=API2
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 *> edit credentials
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 credentials *> set type=CyberArkVaultCredential
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 credentials *> set queryString="Safe=Apis;Folder=Root\Service2;Object=ApiClient"
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 credentials *> set vault=MyCyberArk1
delphix source "pomme" update operations.postRefresh 0 credentialsEnvVarsList 1 credentials *> commitUpon execution, the hook receives two sets of environment variables with corresponding credentials:
API1_PASSWORDwith valueAPI-KEY-02a0b73f.
Variables:
API2_USERAPI2_PASSWORDcontaining the values stored in the vault MyCyberArk1 at the location of the provided query string. The API2 credentials are retrieved from the vault just before the hook executes, so they will always contain the latest values.
